I recently saw the dev.to published REST APIs.
https://developers.forem.com/api
I'm a big fan of dev.to, I often publish and read articles on it, so it made me curious, and I thought of scanning the Dev.to REST API for vulnerabilities. I used this free and web-based API security tool for the job.
https://apisec-inc.github.io/pentest/
I uploaded their OpenAPI Spec file here and submitted it:
https://raw.githubusercontent.com/apisec-inc/pentest/main/OAS/plugin-redoc-0.yaml
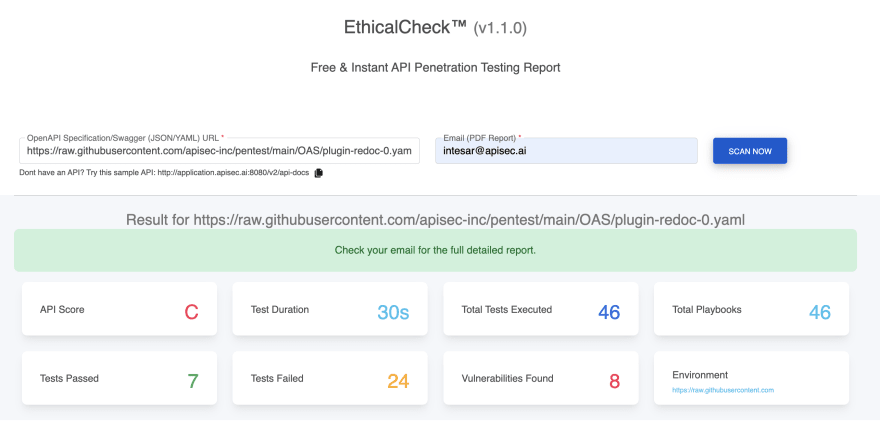
Here are the scan results
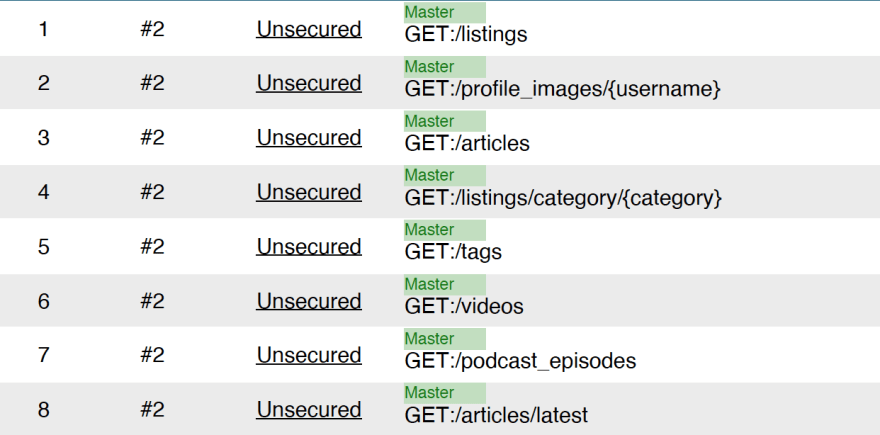
Surprisingly it reported 8 issues. Here is the list:
I analyzed the dev.to web UI to find out what was happening. I quickly figured out all the open endpoints were also open on the web UI and were left public by design so the unauthenticated users can view the dev.to articles, videos, and their associated tags, categories, and authors public images. All other functionality like content engagement, likes, comments, follow, create/manage articles, etc., requires the user to be authenticated.
Conclusion: The free web tool did a decent job of identifying unauthenticated endpoints. But most of the reported endpoints were open by design. Of course, there was no way the tool could have guessed the business reasoning behind leaving those endpoints public.
Here is the free tool link: https://apisec-inc.github.io/pentest/
Comments